$9.44 million, that’s the average cost of a data breach in the US according to IBM. Taking the time to make your application as secure as possible is important. But how do software engineers ensure security in your custom software? And what does this look like in practice?
Today I want to take you through the Software Development Life Cycle (SDLC) and talk about how, at different stages, developers work security concerns into the development process.
To begin, let’s start by describing the different stages of the SDLC.
Table of contents:
- Overview of SDLC phases
- Phases of a secure SDLC: Overview and key activities
- Locking down vulnerabilities: Changing the software processes for higher security
- Secure SDLC- Why software security matters
- Planning and requirements
- Architecture and design
- Test planning
- Coding
- Testing and results
- Release and maintenance
- Increased software security
- Stakeholder awareness of security considerations
- Early detection of design flaws
- Cost reduction through defect resolution
- Decreased business risks
- To protect against an SQL injection, read-only SQL queries to read data from the database and minimize the chances that they are manipulated.
- Validating user inputs before processing data.
- Sanitizing any data that’s being sent back out to the user from the database.
- Checking open-source libraries for vulnerabilities before using them.
- Automated tests that focus on the most important parts of your application.
- Automate the execution of unit tests to ensure the accuracy of your application.
- Employ automated deployment tools that securely manage application secrets in a production environment.
- Conduct penetration tests with the help of specialized external third-party experts.
Overview of SDLC phases
In general, SDCLs include multiple stages:
At every stage, to promote SDLC security, there is a different set of tools. Below is a breakdown of some of the different tests and analyses software engineers use during software development. I will give a brief breakdown of the main areas in the next section.
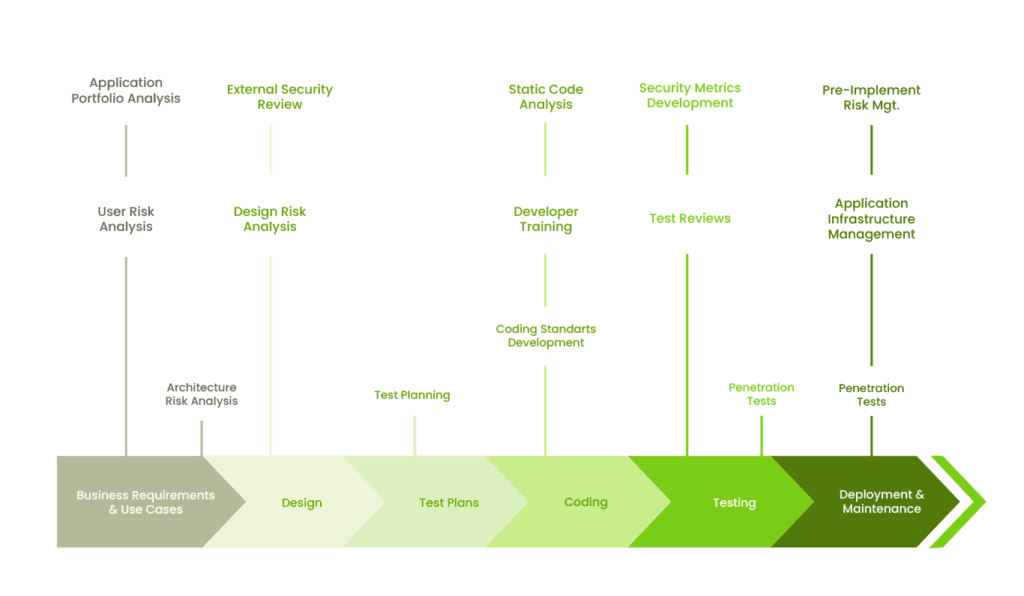
Phases of a secure SDLC: Overview and key activities
To make it easier to understand I will focus on the three main stages, Architecture and design, coding, and deployment. During each stage the security focus shifts, let’s have a closer look at how that works in practice.
Role of architecture analysis in implementing a secure SDLC approach
Implementing a secure SDLC approach starts with architecture analysis during the design phase. This involves assessing the system’s design and identifying security vulnerabilities. It’s important to take the time to ask questions about the final product from the product owner.
Is it an internal system or will it be exposed to the Internet? What user roles will use the system? Where will the system be deployed? Cloud or in-house?
By analyzing the architecture early on, developers can address flaws and weaknesses, integrating security into the software’s foundation.
Importance of conducting code reviews for security
Conducting code reviews during coding and building is crucial for security. Experienced Tech leaders examine the source code to identify and fix vulnerabilities like improper input validation, weak encryption, and insecure database queries. Regular code reviews promote good coding practices and enhance software quality.
The use of integrated development environments (IDE) also helps to boost security. Essentially, an IDE acts as a companion for developers, simplifying the coding process and enhancing productivity. By using supporting plugins such as Sonar, SonarLint, FindBugs, and PMD, developers can check the code automatically for weaknesses.
Understanding penetration testing and ethical hacking
Penetration testing, or ethical hacking, is essential in a secure SDLC approach. It simulates real-world cyber-attacks to evaluate the system. By actively exploiting security measures, engineers can identify entry points for attackers and strengthen their defenses before software release.
It’s crucial to address OWASP’s top 10 attacks during tests and choose appropriate tools for verification. These attacks are like the notorious troublemakers of the cybersecurity world. By staying updated on the latest OWASP top 10 vulnerabilities and using the right tools to verify and test our systems, it ensures increased security.
How does this benefit your project?
Some of the benefits of this approach are:
Locking down vulnerabilities: Changing the software processes for higher security
There is, however, more to talk about with security in software development. If the application deals with sensitive information, then the software delivery process can be adapted. I want to take the time to go through the different stages and describe how software engineers promote additional security.
1. Security in the discovery phase
During the initial phase of development, we prioritize gathering requirements for new features from multiple stakeholders. It is crucial to thoroughly consider security considerations while collecting functional requirements for the upcoming release. Here is an example:
Functional requirement: user needs the ability to verify their contact information before they can renew their membership.
Security consideration: users should be able to see only their contact information and no one else’s. Additionally, the backend API should take requested data from the logged-in user by using OAuth/JWT data.
In short, every feature has a list of security considerations.
2. Security in the design phase
In the design phase features are translated into how they would look in the app. Again, for every functional requirement, there is a security consideration. But in this stage functional designs typically describe what should happen, while security considerations usually focus on what shouldn’t. Below is an example:
Functional design: page should retrieve the user’s name, email, phone, and address from the CUSTOMER_INFO table in the database and display it on screen.
Security consideration: we must verify that the user has a valid session token before retrieving information from the database. If absent, the user should be redirected to the login page.
3. Security in the development phase
When it comes to development the focus shifts across to the code. How well-written the code is will impact security. Here, working to coding guidelines is key. There are also regular code reviews, manual and automatic, that check if the guidelines have been followed.
Some examples of secure coding guidelines are:
Applications may use existing free open-source components to add new features quickly. Most deployed applications rely on these components. To ensure their security, developers use Software Composition Analysis (SCA) tools to check for issues.
4. Agile management and its impact
Using Agile means that software development is more flexible and works around a short period of production known as a sprint, usually two weeks. In Agile software development, security steps are repeated throughout the process, alongside different iterations of the product. However, there can be dedicated Security Sprints that focus solely on security considerations, in addition to the regular sprints.
5. Security in the verification phase
During the Verification phase, applications undergo testing to ensure they match the initial design. This is an ideal opportunity to incorporate automated security testing using various technologies. The application is only deployed if these tests are successful. This phase often involves automated tools, such as CI/CD pipelines, to manage the verification and release processes.
Verification may include:
6. Security during release and maintenance
The work doesn’t stop once the application is released. Vulnerabilities can be discovered even after the release, either in the code written by developers or in the underlying open-source components. These discoveries often lead to an increase in “zero-day” vulnerabilities, which were previously unknown.
The development team needs to patch these vulnerabilities, sometimes requiring significant changes to the application’s functionality. Additionally, vulnerabilities can also be identified through external penetration tests or “bug bounty” programs. It is important to plan and address these production issues in future releases.
Secure SDLC- Why software security matters
Securing software applications is crucial in today’s digital landscape. Throughout the Software Development Life Cycle (SDLC), security is integrated at every step to ensure strong protection. Analyzing architecture, conducting code reviews, and performing penetration tests identify and address vulnerabilities proactively. This approach enhances software security, detects design flaws early, reduces costs, and minimizes business risks.