Signing git commits can be a life-saver when you have to prove that you (or not) are the author of commits or that a commit was changed by the other person. There are few simple yet not, so obvious steps needed to make it work.
Generate your public/private key pair
Run gpg:
gpg --full-gen-key # gpg 2.x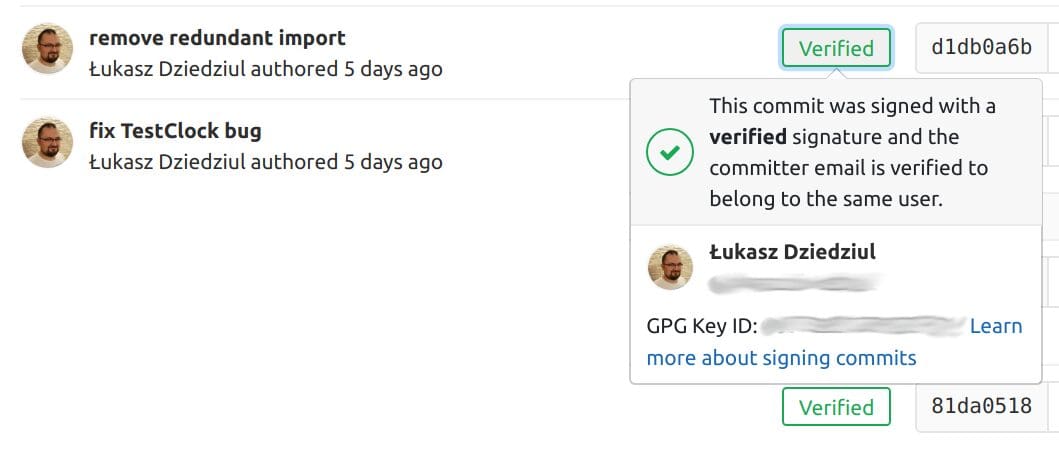
or
gpg --gen-key # gpg 1.x
- Choose
RSA and RSA - Set keysize to
4096 - Set validity period of your key (whatever suits you)
- Enter your details (name and email). It should match your committer identity, otherwise you’ll have to manually inform git which key to use
Export your public key
- Get your public key by running:
gpg --list-secret-keys --keyid-format LONGFind your key and copy the ID, it’s preceded by
sec 4096R/:sec 4096R/123456789ABCDEF0Then run export command:
gpg --armor --export 123456789ABCDEF0and copy the output with your public key (along with
-----BEGIN PGP PUBLIC KEY BLOCK-----and-----END PGP PUBLIC KEY BLOCK-----).
Add a public key to git repository
Github
Go to your profile settings, to SSH and GPG keys section and click on New GPG key where you can paste and save your key.
Gitlab
Go to user settings, to GPG keys, paste your key and press Add key
Setup your local repository and tools
Git repositories are aware about your keys now, but we need to instruct git to use your key
Forcing which public key use to sign
In case of a mismatch between your git user email and email used for gpg keys, you can be explicit about the key used for signging:
git config --global user.signingkey 123456789ABCDEF0
Configure your IDE
In case committing with IDE like IntelliJ you have to configure the gpg to not use the terminal but rather it’s own GUI. Just add the following line to ~/.gnupg/gpg.conf file:
no-tty
On the other hand, it will lead to problems with committing using an ssh session, thus be aware that you have to switch on/off this option depending on whether or not you’re working remotely.
Sign commit
We can do it both ways:
- Add
-Sswitch each time to sign a commit:git commit -S -m add new feature - Configure git to use signing as the default option:
git config --global commit.gpgsign trueIn case of a linux distribution using
gpg2you have to set it explicitly:git config --global gpg.program gpg2
Checking signatures
You can easily see which commits are signed and verified by using gitlab and GitHub repository pages. Every signed commit will have a nice green Verified label. The other option to check it is to use git log command:
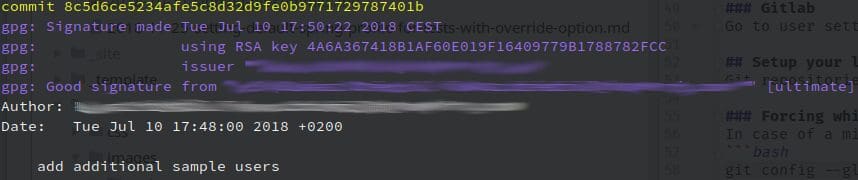
git log --show-signature
After each signed commit, you’ll see info from gpg about the status of the given commits (is it verified or not):
More info:
- https://help.github.com/articles/adding-a-new-gpg-key-to-your-github-account
- https://docs.gitlab.com/ee/user/project/repository/gpg_signed_commits/index.html
- https://git-scm.com/book/en/v2/Git-Tools-Signing-Your-Work
Would you like to talk with our experts about custom software development solutions for your business?
Q: How do I export my public key?
To export your public key, run the command “gpg –list-secret-keys –keyid-format LONG” to find your key ID, and then run the command “gpg –armor –export [key ID]” to export your public key.
Q: How do I add my public key to my git repository?
To add your public key to your git repository on Github, go to your profile settings, to SSH and GPG keys section and click on New GPG key where you can paste and save your key. On Gitlab, go to user settings, to GPG keys, paste your key and press Add key.